Setting Up Users and Groups in Cloud Accounts That Do Not Use Identity Domains
For a cloud account in a region not yet updated to use identity domains prior to the creation of the cloud account, users and groups are set up in Oracle Cloud Infrastructure Identity and Access Management (IAM) and Oracle Identity Cloud Service (IDCS).
This section applies only to cloud accounts that do not use identity domains. If you are not sure if your cloud account uses identity domains, see About Setting Up Users and Groups.
For more information about Oracle Cloud Infrastructure IAM, IDCS, and the documentation that provides the information you need, see Documentation to Use for Cloud Identity in Overview of Identity and Access Management in the Oracle Cloud Infrastructure documentation.
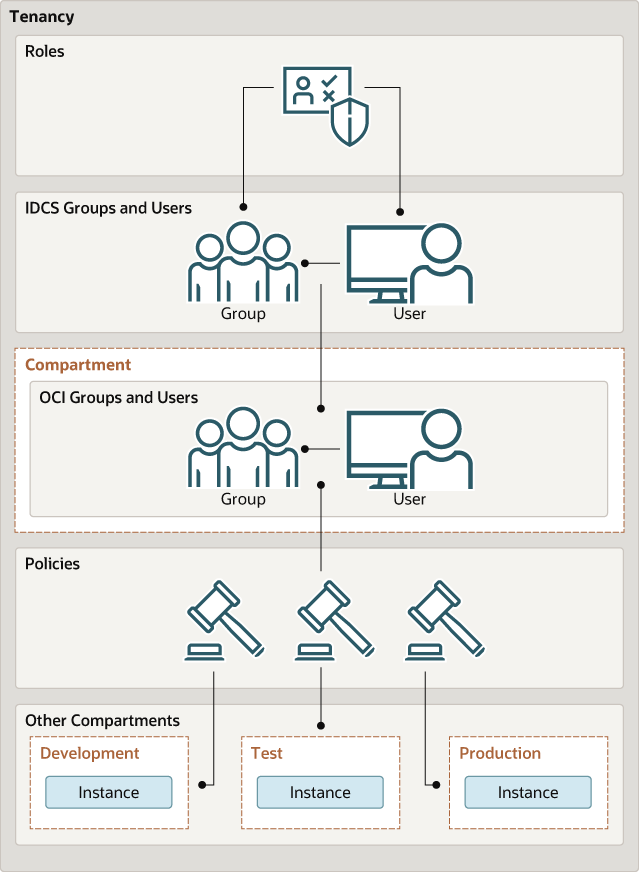
Without identity domains, roles are assigned to IDCS groups, then linked to Oracle Cloud Infrastructure IAM groups using federation, as illustrated in the following diagram.
Understanding Oracle Visual Builder Federation
If your cloud account does not use identity domains, Oracle Cloud Infrastructure Identity and Access Management (IAM) must be federated with Oracle Identity Cloud Service (IDCS) for your tenancy.
User federation refers to linking a user's identity and attributes across multiple identity management systems. Oracle Visual Builder federation means that identities are linked in IDCS and Oracle Cloud Infrastructure Identity and Access Management (IAM).
Oracle Visual Builder uses both IDCS and IAM to manage users and groups:
-
Create and manage users in IDCS. By default, most tenancies are federated with IDCS. For more information about Oracle Identity Cloud Service, see Understanding Administrator Roles in Administering Oracle Identity Cloud Service.
-
Manage permissions using policies in Oracle Cloud Infrastructure's IAM service.
For background information on federation with IDCS, see Federating with Identity Providers and Federating with Oracle Identity Cloud Service.
Whether your tenancy needs federation depends on several factors, such as when your cloud account was created and the Oracle Visual Builder version you're provisioning. Your tenancy may be:
-
Already fully federated: Nearly all accounts in regions that have not yet been updated to use identity domains fall into this category. You'll follow standard steps to set up users and groups, as described in the topics in this section.
-
Mostly federated: If you have an older account that was created before 21 December 2018, you may need to complete a final federation step. You'll follow steps to set up users and groups, as described in the topics in this section. At the mapping step (Mapping the IDCS and OCI Groups), you'll be asked to enter information.
-
Needing federation: If you’re configuring Oracle Visual Builder with a government SKU in a commercial data center, you'll likely need to perform manual federation steps as part of setting up users and groups. See Manually Federating Your Tenancy.
Not sure about your federation? See Is My Tenancy Federated Between Oracle Cloud Infrastructure IAM and Oracle Cloud Identity Service?
Create IDCS Groups and Users
To grant access to Visual Builder instances, assign the users a Visual Builder role. You can grant the role individually to each IDCS user, or create an IDCS group of users and assign the role to the group. You can create Oracle Identity Cloud Service groups for later mapping them to Oracle Cloud Infrastructure Identity and Access Management identities.
Create Oracle Cloud Infrastructure Groups and Policies
To allow other non-admin users to create and manage Visual Builder instances, create an OCI group of non-admin users and assign them the correct OCI policies.
Mapping the IDCS and OCI Groups
You can now map your instance administrator group in IAM to your previously created IDCS group. For details, see Map the IDCS group with the OCI group.
- Open the OCI navigation menu and click Identity & Security. Under Identity, click Federation.
- On the Federation page, select the OracleIdentityCloudService link.
- From the Resources options, choose Group Mapping.
- Click Edit Mapping.
- In the Edit Identity Provider dialog, click Add Mapping
at the bottom.
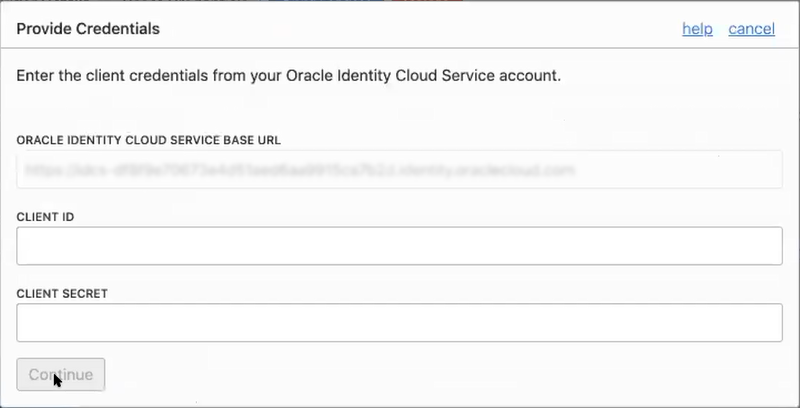
- If the following dialog appears prompting you to provide credentials, enter this information from the COMPUTEBAREMETAL IDCS application in your IDCS account. This dialog indicates that your tenancy is mostly federated and requires only this final step. See Understanding Federation. (If you aren't able to locate this information, file a service request to get help from Oracle Support.)
- Click Continue.
- If the following dialog appears prompting you to provide credentials, enter this information from the COMPUTEBAREMETAL IDCS application in your IDCS account. This dialog indicates that your tenancy is mostly federated and requires only this final step. See Understanding Federation. (If you aren't able to locate this information, file a service request to get help from Oracle Support.)
- Select your IDCS group in the Identity Provider Group field and your OCI group in the OCI Group field.
- Click Submit.
Adding and Assigning Oracle Cloud Infrastructure Users for Read Only Access
After creating a view only group and adding its policy, add users for read only access to Oracle Visual Builder instances.
- Add an OCI user.
- Assign the user to the read only group.
- Select Groups from the Identity options.
- Select the read only group you created (for example,
oci-visualbuilder-viewers). - Click Add User to Group.
- In the Add User to Group dialog, select the user you created and click Add.
- Create the user's password.
- From the Group Members table on the Group Details screen, select the user you added.
- Click Create/Reset Password. The Create/Reset Password dialog is displayed with a one-time password listed.
- Click Copy, then Close.
- Provide read only users the information they need to sign in.
Assigning Oracle Visual Builder Service Roles to Groups
After a Visual Builder instance has been created, assign Visual Builder roles to groups of users in Oracle Visual Builder to allow them to work with the features of the Visual Builder instance.
It's a best practice to assign Visual Builder service roles to selected groups rather than individual users.
Oracle Visual Builder provides a standard set of set of service roles, which govern access to features. Depending on the Visual Builder features your organization uses, you may choose to create groups named for the service role they are granted. For example, VBServiceAdministrators for administration permissions.