Manage Master Encryption Keys in AWS Key Management Service
Autonomous AI Database supports customer-managed Transparent Data Encryption (TDE) keys that reside in AWS Key Management Service (KMS).
- Prerequisites to Use Customer-Managed Encryption Keys in AWS Key Management Service
Describes prerequisite steps to use customer-managed master encryption keys that reside in Amazon Web Services (AWS) Key Management Service (KMS) on Autonomous AI Database. - Use Customer-Managed Encryption Keys on Autonomous Database with AWS Key Management Service
Shows the steps to encrypt your Autonomous AI Database using customer-managed master encryption keys that reside in AWS Key Management Service (KMS).
Parent topic: Manage Encryption Keys on Autonomous AI Database
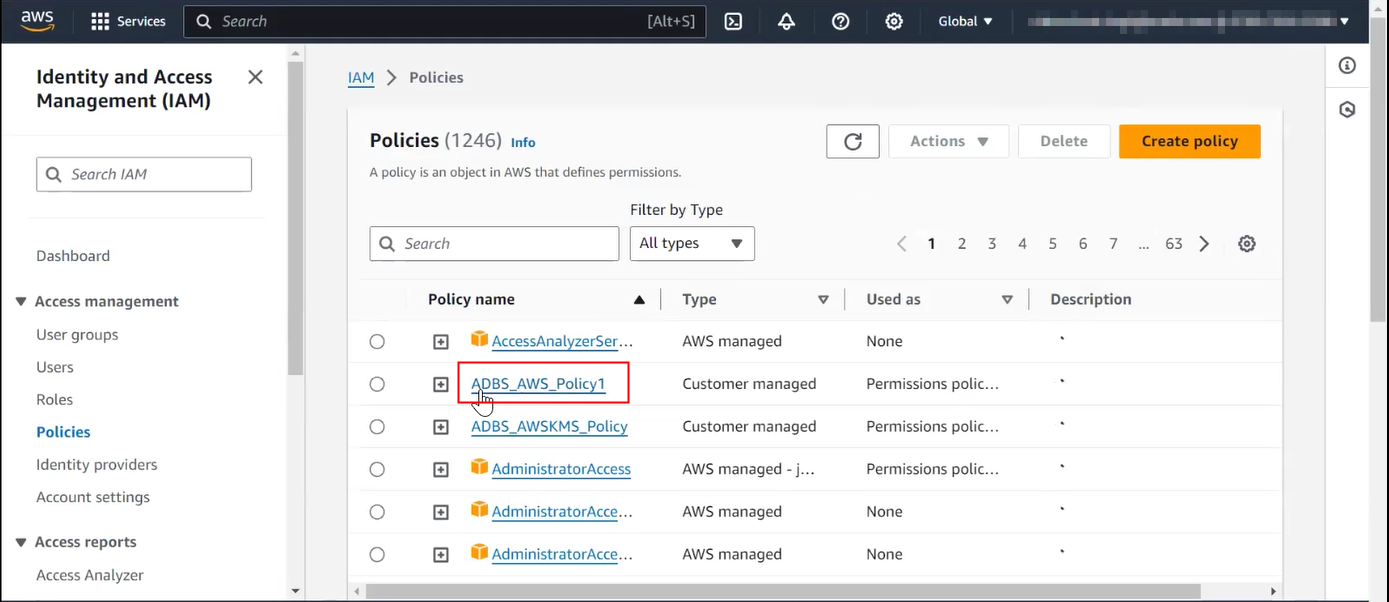
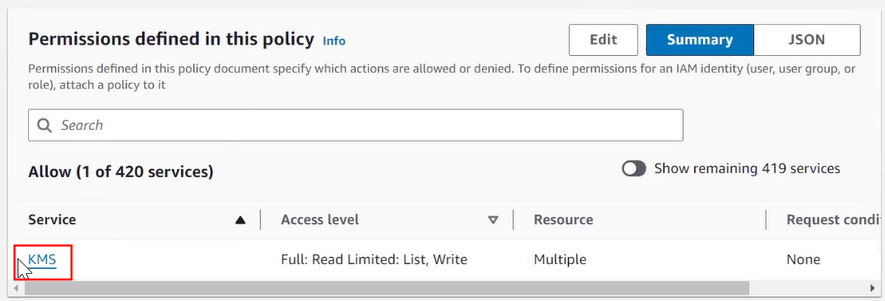
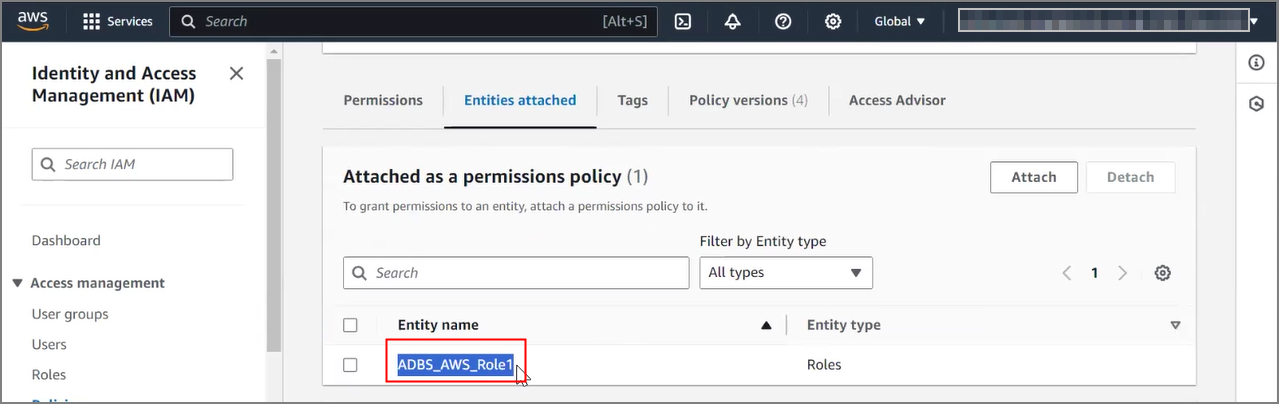
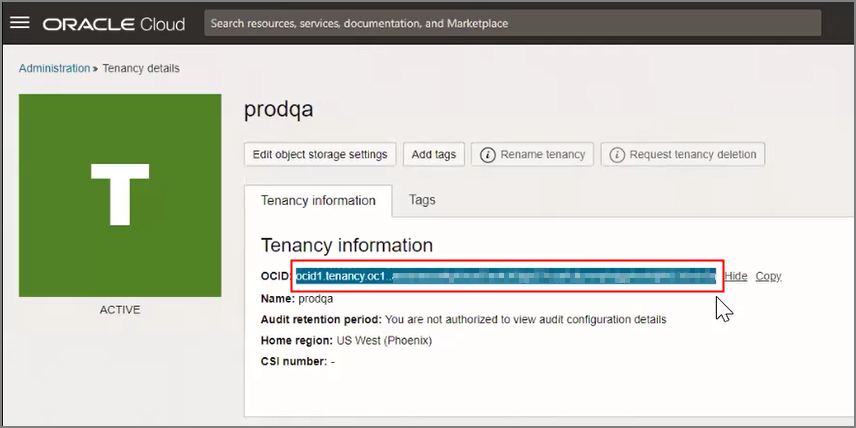
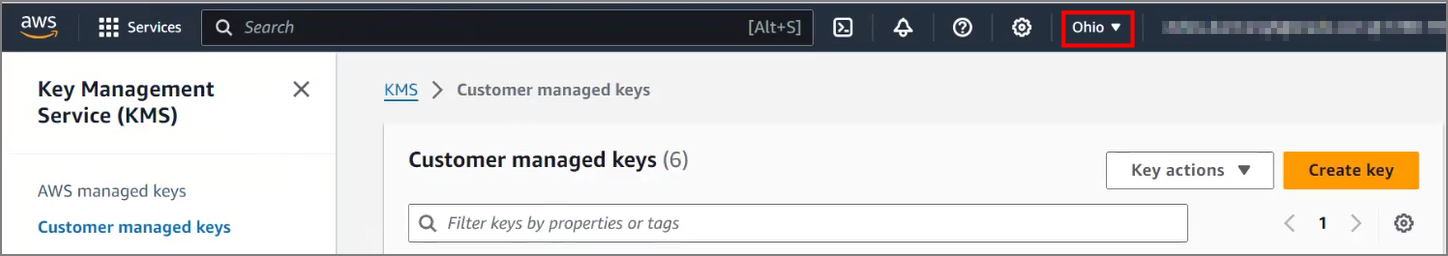
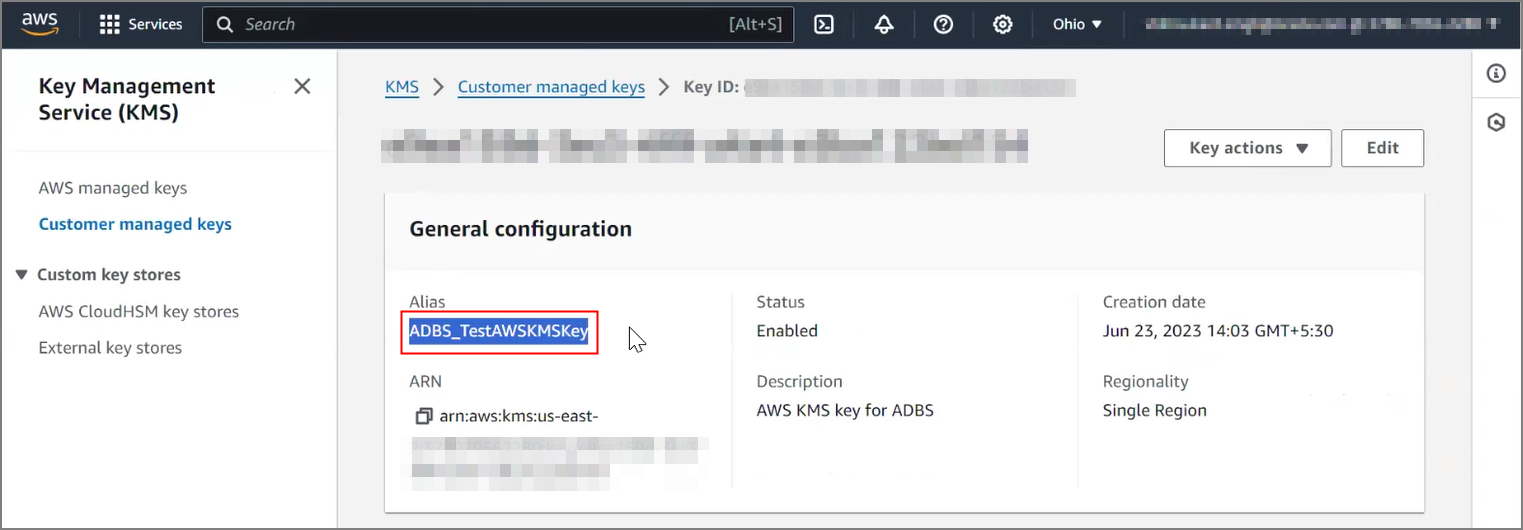
Prerequisites to Use Customer-Managed Encryption Keys in AWS Key Management Service
Describes prerequisite steps to use customer-managed master encryption keys that reside in Amazon Web Services (AWS) Key Management Service (KMS) on Autonomous AI Database.
- AWS KMS is only supported in commercial regions.
- AWS KMS is not supported in cross-region Autonomous Data Guard standbys.
Follow these steps:
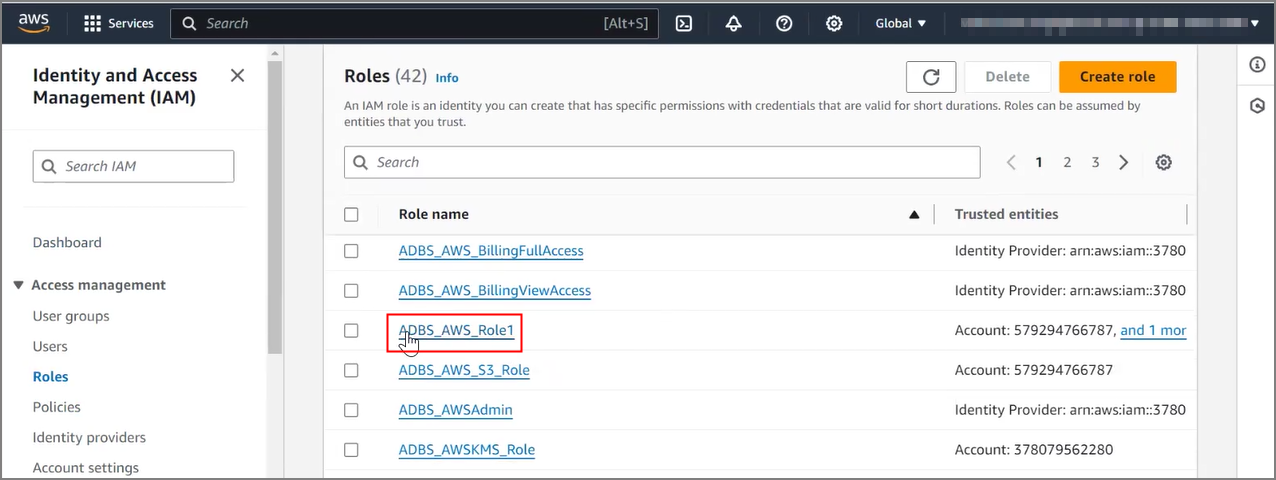
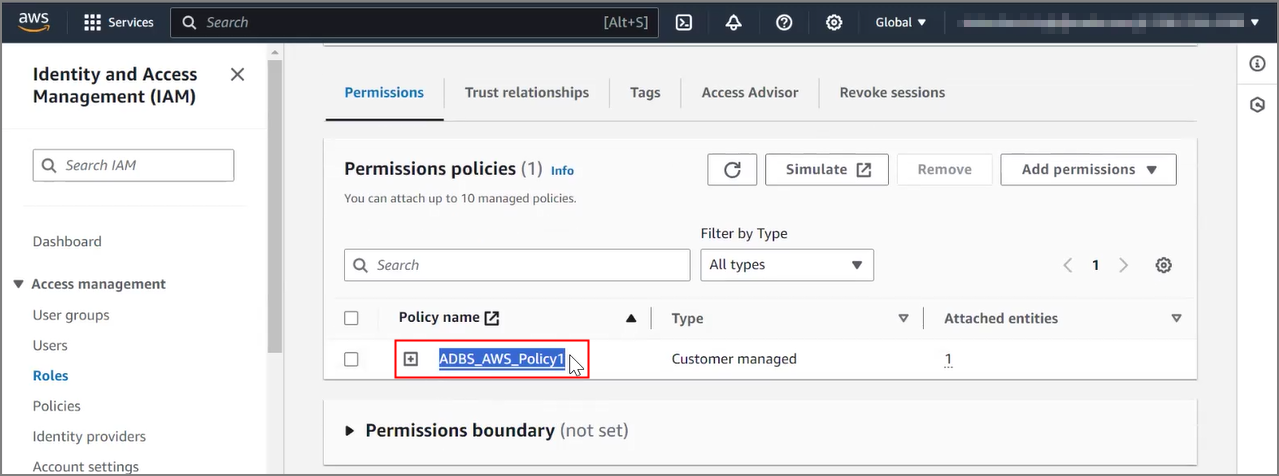
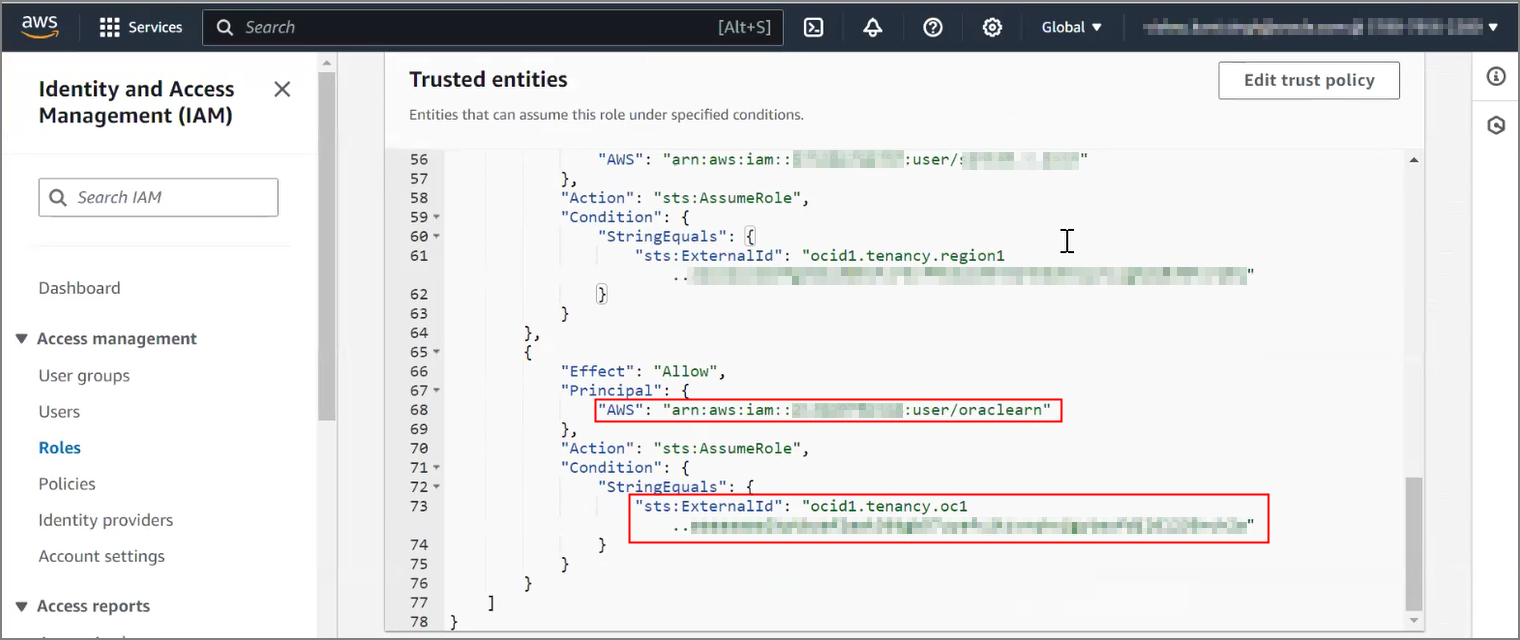
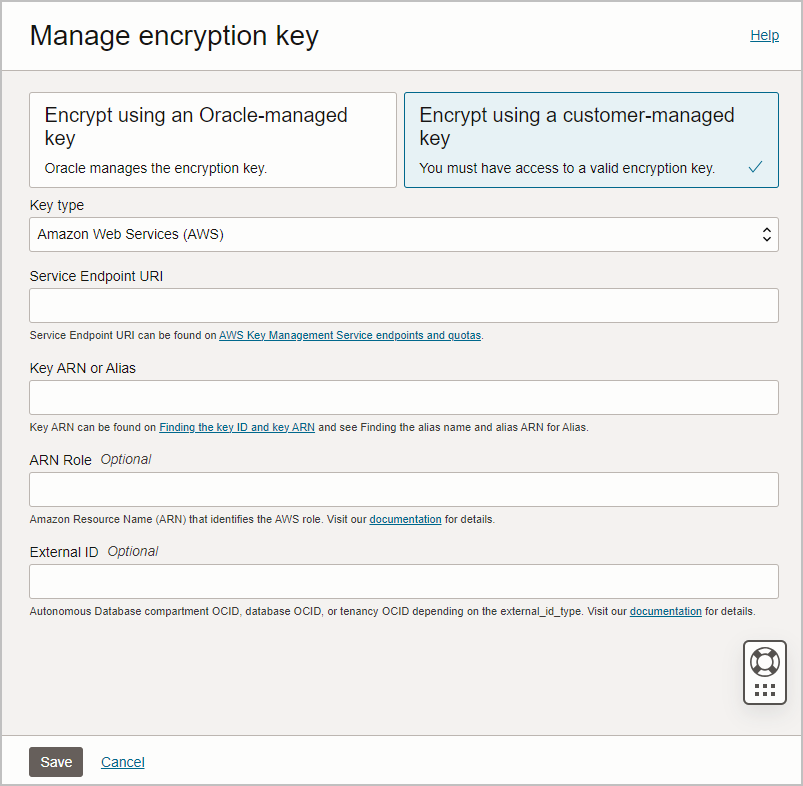
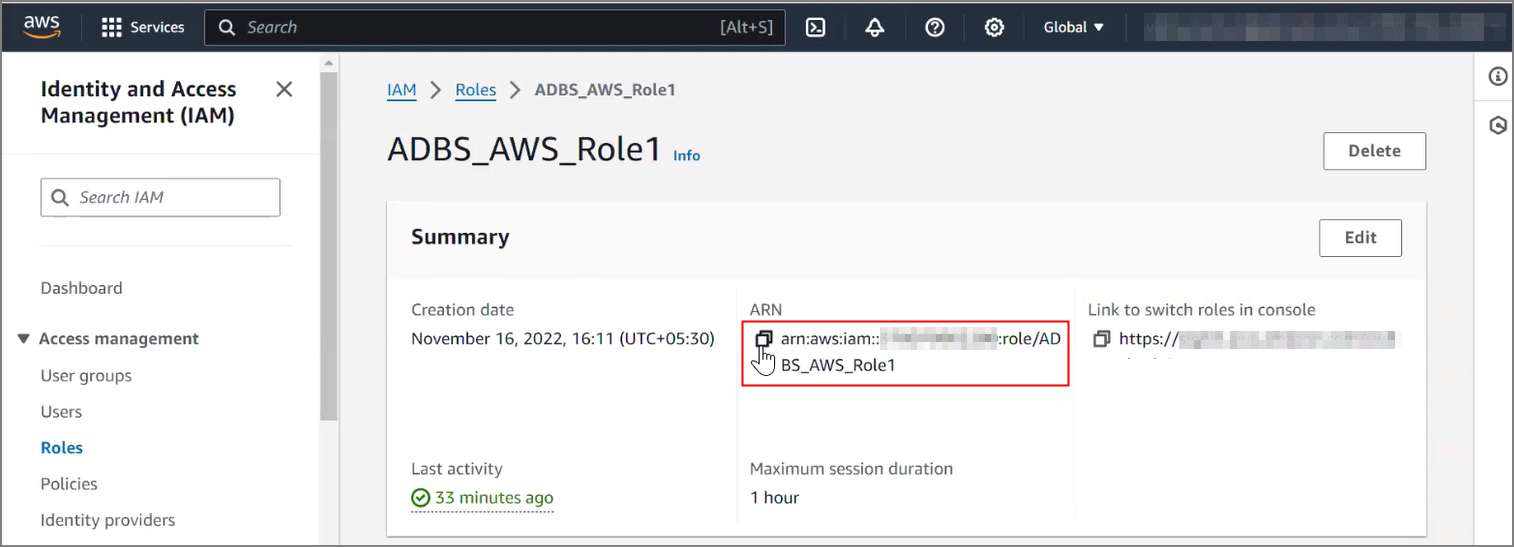
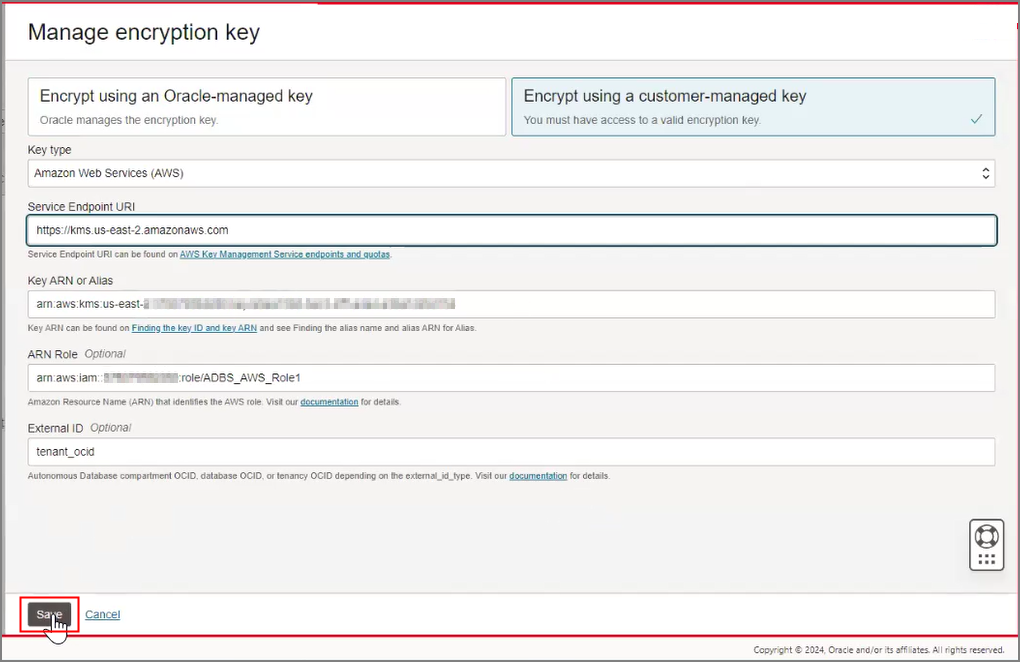
Use Customer-Managed Encryption Keys on Autonomous Database with AWS Key Management Service
Shows the steps to encrypt your Autonomous AI Database using customer-managed master encryption keys that reside in AWS Key Management Service (KMS).
Follow these steps:
The Lifecycle state changes to Updating. When the request completes, the Lifecycle state shows Available.
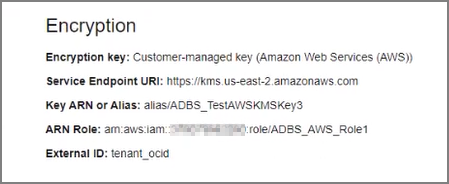
After the request completes, on the Oracle Cloud Infrastructure Console, the key information shows on the Autonomous Database instance details page under the heading Encryption.
For example:
See Notes for Using Customer-Managed Keys with Autonomous AI Database for more information.