Set Up OCI Terraform
Set up Oracle Cloud Infrastructure Terraform provider scripts, documented in the Terraform Registry, to connect to an OCI account. Confirm the setup by fetching information from the tenancy.
Key tasks include how to:
- Create RSA keys.
- Set up Oracle Cloud Infrastructure Terraform provider scripts:
- Authenticate your Terraform scripts.
- Get information about the availability domains in your tenancy.
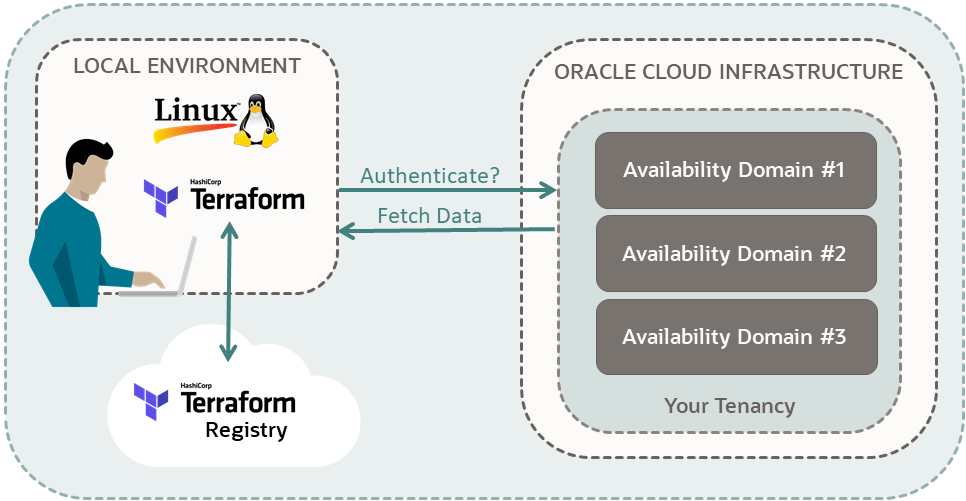
For more information, see:
Before You Begin
To successfully perform this tutorial, you must have the following:
- An Oracle Cloud Infrastructure account. See Request and Manage Free Oracle Cloud Promotions.
- A MacOS, Linux, or Windows environment:
- MacOS
- Linux (Any distribution)
- You can install a Linux VM with an Always Free Compute shape, on Oracle Cloud Infrastructure. See Free Tier: Install Apache and PHP on an Oracle Linux Instance.
- Oracle Cloud Infrastructure Cloud Shell:
- How to install Linux on Windows with WSL (WSL)
- Git for Windows to access a Linux VM.
This tutorial uses an Oracle Linux VM environment with an AMD shape for its examples, but you can use any environment mentioned in this section.
1. Prepare
Prepare your environment for authenticating and running Terraform scripts. Also, gather the information your account needs to authenticate the scripts.
Skip creating RSA keys if:
- You're using Cloud Shell or Resource Manager. You're already authenticated when you sign in to the Oracle Cloud Console.
- You already created RSA keys for the tutorial Set Up Resource Discovery.
You have now set up the RSA keys to connect to your OCI account.
- Reference
- How to Generate an API Signing Key
If your username is in the Administrators group, then skip this section. Otherwise, ask your administrator to add the following policy to your tenancy:
allow group <a-group-that-your-username-belongs-to> to read all-resources in tenancyWith this privilege, you can list all the resources in your tenancy.
- Sign in to the Oracle Cloud Console.
-
In the navigation menu , select the Profile menu
 and then select User settings.
and then select User settings.
- Select Groups or My groups, depending on the option that you see.
- In a notepad, copy the name of a group that your username belongs to.
- Open the navigation menu and select Identity & Security. Under Identity, select Policies.
- Select the compartment:
<your-tenancy>(root) - Select Create Policy.
- On the Create Policy page, enter the following values:
-
Name:
list-resources -
Description:
Allow the group <a-group-that-your-username-belongs-to> to list the resources in this tenancy. -
Compartment:
<your-tenancy>(root)
-
Name:
- For Policy Builder, select Show manual editor.
- Paste in the following policy:
allow group <a-group-that-your-username-belongs-to> to read all-resources in tenancy - Select Create.
Reference: Common Policies
Prepare the information you need to authenticate your Terraform scripts and copy the information into a notepad.
2. Create Scripts
Create scripts for authentication, to fetch data from your account, and to print outputs.
required_providers block to declare required provider versions.Use the following variables for API Key based authentication:
-
tenancy_ocid -
user_ocid -
private_key_path -
fingerprint -
region
You don't need to install the provider. The provider is downloaded when you run the scripts in this tutorial.
provider.tf script and you get information from your account.In Terraform, to fetch data, you use a data source. Fetching data from a data source is similar to the GET method in REST APIs.
- Go to Oracle Cloud Infrastructure Provider.
-
In the Filter box on the upper left, enter
availability domains. - Under Identity, go to Data Sources and select oci_identity_availability_domains.
The title of the page is the resource type:
oci_identity_availability_domains - Find the Data Source name from the title of the page:
- Data Source:
- In the Argument Reference section, find all arguments (inputs) labeled as (Required):
- compartment_id
- Construct a data source block:
- Declare a data source with the keyword:
data. - Add a label for the data source name:
"oci_identity_availability_domains" - Add a label of your choice for the local name:
-
The label can contain letters, digits, underscores (
_), and hyphens (-). The first character must not be a digit. - This tutorial uses the local name,
"ads"to constructdata "oci_identity_availability_domains" "ads".
-
The label can contain letters, digits, underscores (
- Inside the code block, provide values for all required arguments.
- Example:
compartment_id = "<some-compartment-ocid>"
- Example:
- For optional arguments, provide values to narrow down the fetch results. Only some data sources have optional arguments.
- Declare a data source with the keyword:
The data source oci_identity_availability_domains, fetches a list of availability domains. In this section, you declare an output block to print the fetched information.
- Go to Attributes Reference (oci_identity_availability_domains).Note
Attributes are the outputs that you can return for theoci_identity_availability_domainsdata source. - Find the attributes:
- Attribute:
availability_domains:- The list of availability domains
- If you output
availability_domains:, you get three attributes for each availability domain in the list:- compartment_id
- id
- name
- Attribute:
- Construct a data source output block:
- Declare an output block with the keyword:
output - Add a label to be printed with the output results:
-
The label can contain letters, digits, underscores (
_), and hyphens (-). The first character must not be a digit. - Example:
"all-availability-domains-in-your-tenancy"
-
The label can contain letters, digits, underscores (
- Inside the code block, enter a value for the data source output with the expression:
-
value = data.<data-source-name>.<local-name-for-data-source>.<attribute> - Example:
value = data.oci_identity_availability_domains.ads.availability_domains
-
- Declare an output block with the keyword:
3. Run Scripts
Run your Terraform scripts. After your account authenticates the scripts, Terraform fetches your tenancy's availability domains.
tf-provider directory.You now have a folder called .terraform that includes the plugins for the oci provider.
plan command.
terraform planExample output:
data.oci_identity_availability_domains.ads: Reading...
data.oci_identity_availability_domains.ads: Read complete after 1s [id=xxx]
Changes to Outputs:
+ all-availability-domains-in-your-tenancy = [
+ {
+ compartment_id = "ocid1.tenancy.oc1..xxx"
+ id = "ocid1.availabilitydomain.xxx"
+ name = "QnsC:US-ASHBURN-AD-1"
},
+ {
+ compartment_id = "ocid1.tenancy.oc1..xxx"
+ id = "ocid1.availabilitydomain.yyy"
+ name = "QnsC:US-ASHBURN-AD-2"
},
+ {
+ compartment_id = "ocid1.tenancy.oc1..xxx"
+ id = "ocid1.availabilitydomain.zzz"
+ name = "QnsC:US-ASHBURN-AD-3"
},
]
You can apply this plan to save these new output values to the Terraform state, without changing any real
infrastructure.
- You're fetching data, so the plan shows that you're only adding outputs. You're not adding, changing, or destroying any resources.
- You're using the
output.tffile instead of the-outoption, so you can ignore the following message:Note: You didn't use the -out option to save this plan, so Terraform can't guarantee to take exactly these actions if you run "terraform apply" now.
Congratulations! Your Oracle Cloud Infrastructure account can now authenticate your Oracle Cloud Infrastructure Terraform provider scripts.
References:
You might encounter the following error messages while running your Terraform scripts.
401 Errors - (Service error:NotAuthenticated)
One of the following variables has an incorrect value:
- Tenancy OCID
- User OCID
- Fingerprint
- RSA private key (the path or the key)
Can not create client, bad configuration: did not find a proper configuration for private key
The Terraform scripts can't find the RSA private key.
No such host
The region identifier has an incorrect value.
Failed to query available provider packages
If you're on a VPN, check the proxy settings.
What's Next
For the next Terraform: Get Started tutorial, go to:
To explore more information about development with Oracle products, check out these sites: