Cross-Tenancy Association Policies
Your organization may also want to create connections in its tenancy that reference private endpoints in another tenancy, or allow its own private endpoints to be used by connections in another tenancy.
To allow an IAM group to create such cross-tenancy connections, the tenancy administrators must write special "cross-tenancy association" policy statements. These statements use the Endorse and Admit verbs as with normal cross-tenancy policy statements, but instead of granting permission to perform an action such as read or use on one type of resource, they grant permission to associate two types of resources with one another.
Cross-Tenancy Association Statements
Cross-tenancy association policy statements are required:
- When a group creates a connection referencing a private endpoint that is not in the same tenancy as the connection, or updates an existing connection to make such a reference.
- In addition to the normally required cross-tenancy policy statements. For example, cross-tenancy statements are required to allow the group to use the private endpoint if it is in a different tenancy than the group.
- Only for certain pairs of resources. Database Tools only requires them for connections and private endpoints. They are not required for all pairs of resources that can reference one another, such as connections and vault secrets.
Once the connections are created, cross-tenancy association policies are not required to use them. Any user with permission to use the connections and read the referenced secrets is able to use the connections.
In the following examples, we refer to the tenancy with the group and connection as the group tenancy, and the tenancy with the private endpoint as the resource tenancy.
This is an example of a possible configuration where cross-tenancy association policy statements are required. The connections are created in a different tenancy than the private endpoints they reference.
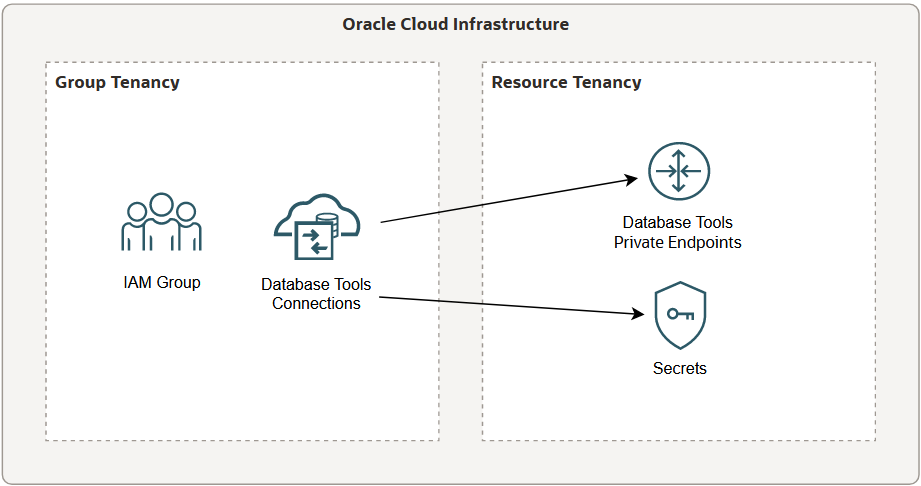
It is also possible to have the secrets in the group tenancy, or to switch the connections and private endpoints. If the connections and private endpoints are together in the same tenancy, you do not need cross-tenancy association policies.
Group Tenancy Policy Statements
As the group tenancy administrator, you create policy statements that:
- Define an alias for the resource tenancy. The resource tenancy administrator must provide the OCID of the resource tenancy.
- Endorse an IAM group in your tenancy to associate connections in your tenancy or compartment with private endpoints in the resource tenancy.
You can also include the normal cross-tenancy policy statements required to endorse the group to access resources in the resource tenancy.
The following is an example of policy statements that endorse the IAM group
DatabaseToolsConnectionManagers to associate connections in a group
tenancy compartment, ConnectionsCompartment, with private endpoints in
ResourceTenancy. They also endorse the group to read secrets and
use private endpoints in ResourceTenancy:
Define tenancy ResourceTenancy as <resource_tenancy_ocid>
Endorse group DatabaseToolsConnectionManagers to associate database-tools-connections in compartment ConnectionsCompartment with database-tools-private-endpoints in tenancy ResourceTenancy
Endorse group DatabaseToolsConnectionManagers to read secret-family in tenancy ResourceTenancy
Endorse group DatabaseToolsConnectionManagers to use database-tools-private-endpoints in tenancy ResourceTenancy
Resource Tenancy Policy Statements
As the resource tenancy administrator, you create policy statements that:
- Define aliases for the group tenancy and the IAM group that is allowed to access resources in your tenancy. The group tenancy administrator must provide the OCIDs of the group tenancy and group.
- Admit the group to associate connections in the group tenancy with private endpoints in your tenancy or compartment.
You can also include the normal cross-tenancy policy statements required to admit the group to access resources in your tenancy.
The following is an example of policy statements that admit the IAM group
DatabaseToolsConnectionManagers in the group tenancy to associate
connections in GroupTenancy with private endpoints in a resource
tenancy compartment, PrivateEndpointsCompartment. They also admit the
group to read secrets and use private endpoints in
PrivateEndpointsCompartment:
Define tenancy GroupTenancy as <group_tenancy_ocid>
Define group DatabaseToolsConnectionManagers as <database_tools_connection_managers_group_ocid>
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to
associate database-tools-connections in tenancy GroupTenancy with
database-tools-private-endpoints in compartment PrivateEndpointsCompartment
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to read
secret-family in compartment PrivateEndpointsCompartment
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to use
database-tools-private-endpoints in compartment PrivateEndpointsCompartment
With Three Tenancies
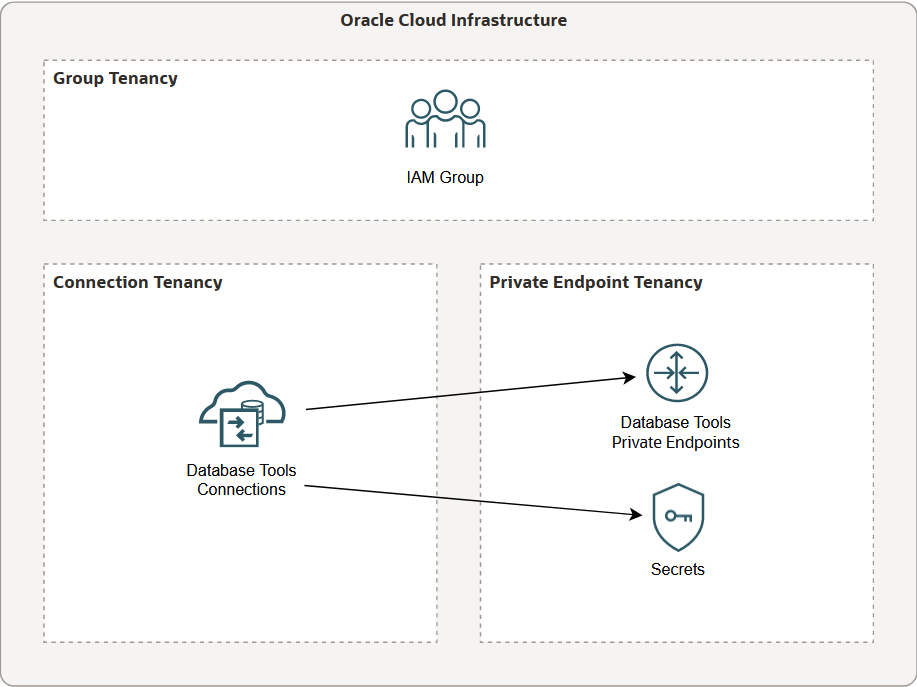
The IAM group can also be in a third tenancy. Suppose the group is in a
tenancy called GroupTenancy, the connections are in a tenancy called
ConnectionTenancy, and the private endpoints are in a tenancy
called PrivateEndpointsTenancy.
Since there are three tenancies, three cross-tenancy association policy statements are
required. Besides additional Define statements, GroupTenancy
must have an Endorse statement, and ConnectionTenancy and
PrivateEndpointsTenancy must each have an Admit statement.
This is an example of a possible configuration involving three tenancies. The group, connections, and private endpoints are all in separate tenancies. Other possible configurations could have the secrets in one of the other tenancies or even in a fourth tenancy, but cross-tenancy association policies are not required for connections and secrets.
The following is an example of policy statements in
GroupTenancy that endorse an IAM group in the tenancy,
DatabaseToolsConnectionManagers, to associate connections in
ConnectionTenancy with private endpoints in
PrivateEndpointTenancy. It also endorses the group to manage
connections in ConnectionTenancy and read secrets and use private
endpoints in PrivateEndpointTenancy:
Define tenancy ConnectionTenancy as <connection_tenancy_ocid>
Define tenancy PrivateEndpointTenancy as <private_endpoint_tenancy_ocid>
Endorse group DatabaseToolsConnectionManagers to associate
database-tools-connections in tenancy ConnectionTenancy with
database-tools-private-endpoints in tenancy PrivateEndpointTenancy
Endorse group DatabaseToolsConnectionManagers to manage
database-tools-connections in tenancy ConnectionTenancy
Endorse group DatabaseToolsConnectionManagers to read secret-family
in tenancy PrivateEndpointTenancy
Endorse group DatabaseToolsConnectionManagers to use
database-tools-private-endpoints in tenancy PrivateEndpointTenancy
The following is an example of policy statements in
ConnectionTenancy that endorse
DatabaseToolsConnectionManagers to associate connections in the
tenancy with private endpoints in PrivateEndpointTenancy. It also
admits the group to manage connections in a compartment called
ConnectionsCompartment:
Define tenancy GroupTenancy as <group_tenancy_ocid>
Define tenancy PrivateEndpointTenancy as <private_endpoint_tenancy_ocid>
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to
associate database-tools-connections in tenancy with
database-tools-private-endpoints in tenancy PrivateEndpointTenancy
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to manage
database-tools-connections in compartment ConnectionsCompartmentThe following is an example of policy statements in
PrivateEndpointTenancy that endorse
DatabaseToolsConnectionManagers to associate connections in
ConnectionTenancy with private endpoints in the tenancy. It also
admits the group to read secrets and use private endpoints in a compartment called
PrivateEndpointsCompartment:
Define tenancy GroupTenancy as <group_tenancy_ocid>
Define tenancy ConnectionTenancy as <connection_tenancy_ocid>
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to
associate database-tools-connections in tenancy ConnectionTenancy
with database-tools-private-endpoints in tenancy
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to read
secret-family in compartment PrivateEndpointsCompartment
Admit group DatabaseToolsConnectionManagers of tenancy GroupTenancy to use
database-tools-private-endpoints in compartment PrivateEndpointsCompartment