IAM Policies Overview
IAM policies govern control of resources in Oracle Cloud Infrastructure (OCI) tenancies.
A policy contains one or more policy statements. Each statement uses basic or conditional syntax.
Basic syntax:
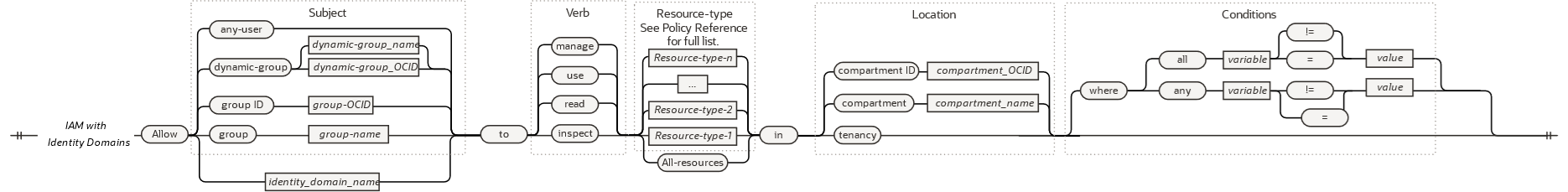
Allow <subject> to <verb> <resource> in <location>Conditional syntax:
Allow <subject> to <verb> <resource> in <location> where <conditions>The following table briefly explains the elements in the syntax and provides links to detailed information about each element.
| Element | Description |
|---|---|
| Allow | Required start word. A policy statement always begins with the word Allow. Policies only allow access; they can't deny it. |
| <subject> |
A user, group, or other principal to be granted access. The subject includes the principal type and identifier (name or OCID), and is prefixed by the name of the identity domain unless the default identity domain is used. An administrator in your organization defines the groups and compartments in your tenancy. |
| <verb> | The level of access. Oracle defines the possible verbs and resource-types you can use in policies, see Verbs. |
| <resource> |
Resources to which the policy grants access. Oracle defines the possible resource-types you can use in policies, see Resources. Some API operations require access to several resource-types. For example, |
| <location> |
(Optional) A compartment or tenancy to which the policy applies. For a compartment, the value includes an identifier (name or OCID). Sometimes the policy needs to apply to the entire tenancy, and not a compartment inside the tenancy. The following is an example of a compartment-specific policy statement, in which the <location> is a specific compartment: Following is an example of a tenancy-wide policy statement, in which the <location> is tenancy: |
| <condition> | (Optional) Limits access to a resource. |
OCI also lets you create cross-tenancy policies. For more information, see Cross-Tenancy Access Policies.
Cross-tenancy Policies
Cross-tenancy policy statements give subjects permission to use resources in other tenancies. See Cross-Tenancy Access Policies.